Why Cloud Compliance Still Fails: The Case for a Federated Inventory
It strikes me, reflecting on my journey in the cybersecurity industry since 1997, that we’re caught in a frustratingly familiar loop. In the early 2000s the mantra was simple: lockdown server configurations, patch diligently, and tick the compliance boxes for SOX or HIPAA. We meticulously documented settings, ran vulnerability scans, and felt safe when the auditors signed off.
Fast‑forward two decades and the technology landscape has exploded with cloud dynamism, yet the core challenge is eerily similar. We’re still wrestling with configuration—cloud misconfigurations, ephemeral assets, and an ever‑growing web of interconnected services. And just like before, we risk mistaking compliance for genuine security. We dutifully check the CIS Benchmarks or SOC 2 boxes, but do we truly understand the security posture of our entire cloud ecosystem?
Analyst reports have long warned that point solutions provide only a keyhole view of infrastructure risk. A single misconfigured firewall rule—or today, an overly permissive IAM policy—can undermine an otherwise “compliant” environment. In the cloud era, that complexity is magnified by shadow IT and assets that appear and vanish in minutes.
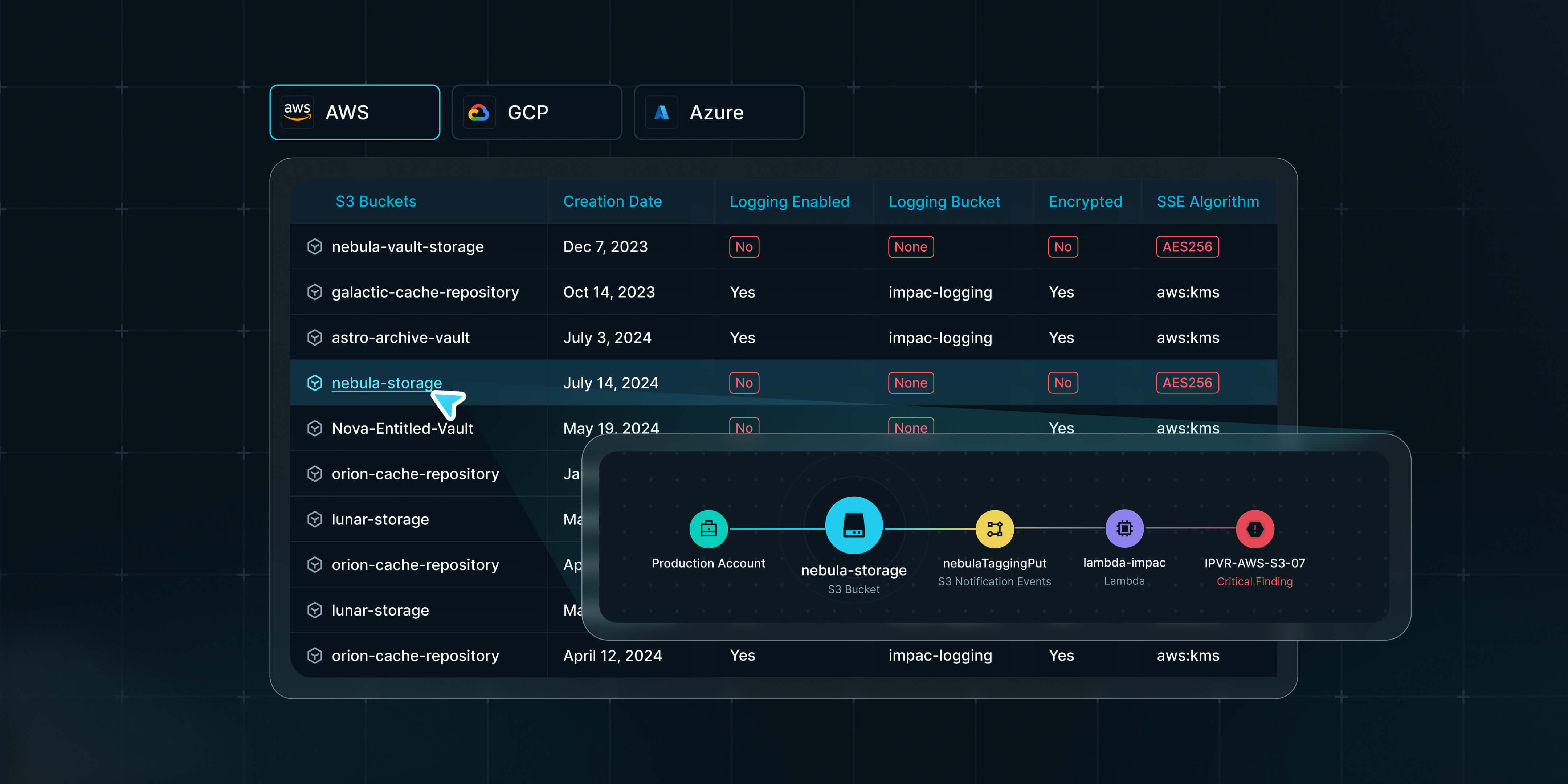
The result? A constantly shifting attack surface that isolated tools struggle to capture. Even best‑of‑breed CloudSecurity Posture Management (CSPM), Cloud‑Native Application ProtectionPlatforms (CNAPP), vulnerability scanners, Identity and AccessManagement (IAM) suites, or Application Security PostureManagement (ASPM) systems operate in silos. An S3 bucket might pass a CSPM check, but if its IAM role is over‑permissive—as Brian’s recent post highlighted—the whole asset becomes a ticking time bomb.
The Path Forward: Federation and Context
The solution lies in a fundamental mindset shift. We need to move beyond a checklist mentality and embrace a federated inventory approach—a living, real‑time map of every asset, from compute instances and containers to serverless functions, data stores, and identities, enriched with findings from all our security tools.
A federated inventory doesn’t just list resources; it understands their relationships and dependencies. It ingests:
- CSPM – surfacing misconfigurations and drift
- CNAPP – analyzing cloud workloads and network policy
- Vulnerability Management – highlighting software weaknesses
- IAM – revealing privilege and trust risks
- ASPM – detailing application‑layer exposure
By weaving these signals together, security teams can see the chain of potential exploits instead of isolated findings and can proactively mitigate risks arising from “compliant” yet insecure combinations.
Security isn’t a zero‑sum game. Our investments shouldn’t compete—they should collaborate. A federated inventory becomes the Rosetta Stone, translating each tool’s language into a unified view of risk, empowering teams to support business goals with confidence.
The challenges of cloud security aren’t new; they’re simply evolutions of problems we’ve faced for decades.Learning from the past and adopting a federated, contextual view will finally bridge the gap between compliance and true security in today’s dynamic cloud era.
The solution lies in a fundamental shift: embracing a federated inventory approach. Imagine a dynamic, real-time map of all assets, enriched with context from various security tools. This holistic view empowers security teams to proactively identify risks and support business goals confidently.
If you agree and want to see how a confluence of security tools works, schedule a live demo with our cloud security engineers and watch a federated inventory inaction. Request a Demo


