Why Security Tools Should Work Like Trading Platforms
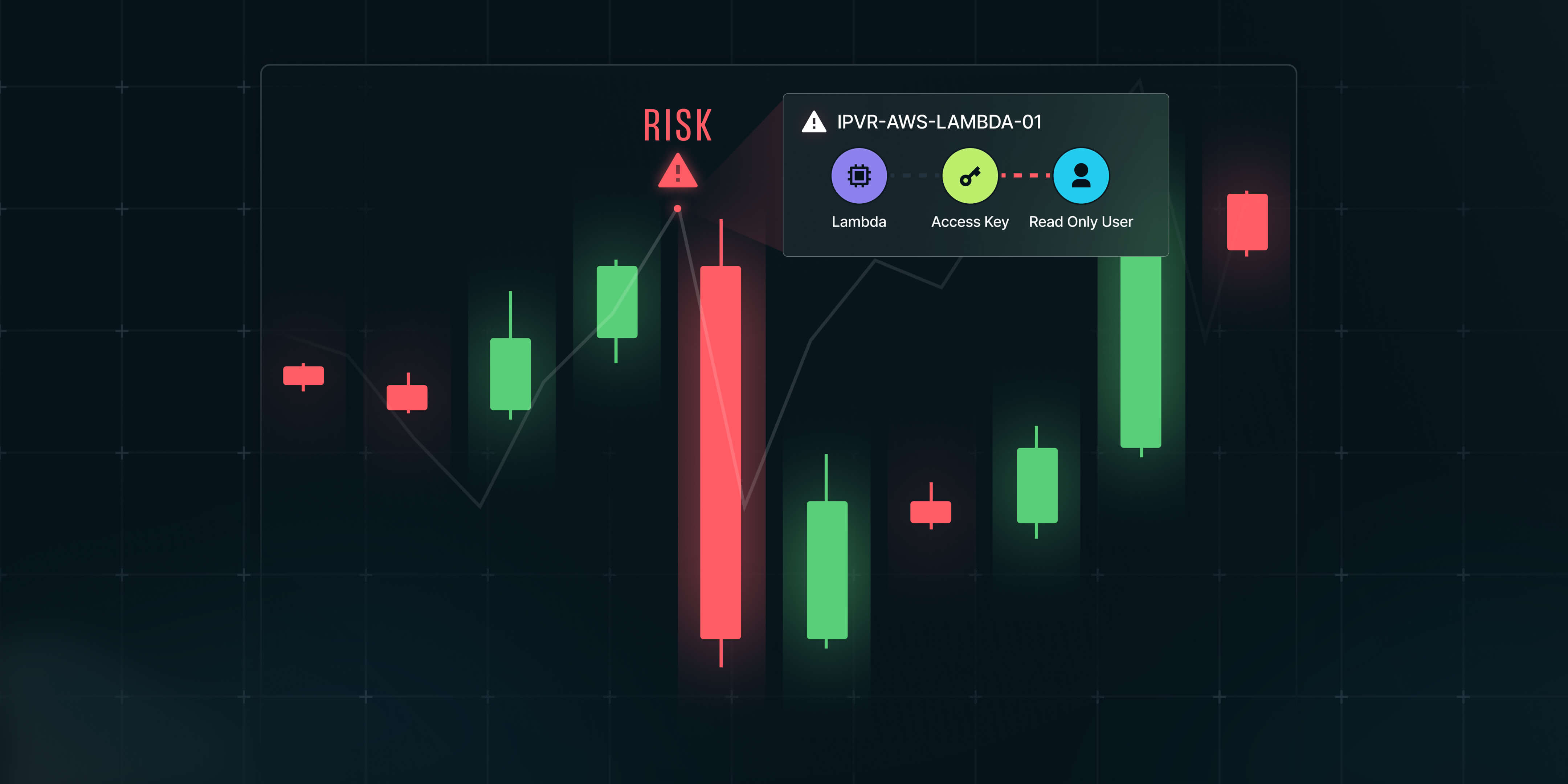
Imagine managing your investment portfolio with a tool that sends thousands of price alerts, but doesn’t show market trends, risk exposure, or let you take action directly. It would be chaotic, slow, and likely very expensive.
Yet that’s how most cloud security tools operate today.
They flood teams with alerts. They silo insights. They offer no meaningful way to act quickly, track outcomes, or visualize risk in context. The result? Slower decisions, higher exposure, and teams working in the dark.
It’s time for security tools to evolve and perhaps take inspiration from an unexpected place: trading platforms.
Traders and Security Teams Have the Same Core Job: High-Stakes, High-Speed Risk Management
Both traders and security teams:
- Monitor signals from a constantly shifting environment
- Evaluate risk based on evolving, interconnected data
- Take rapid, informed action to prevent loss
- Track decisions and outcomes for accountability
But while traders have Bloomberg terminals (dashboards that combine signals, automate actions, and give full historical traceability), security teams are stuck in swivel-chair mode, bouncing between dashboards and spreadsheets just to triage alerts.
What’s Wrong with Security? Signals Without Confluence
Security tools today are fragmented. DSPMs tell you where sensitive data lives. CNAPPs warn you about exposed workloads. Vulnerability scanners raise red flags on patch gaps.
Each is valuable. But none of them talk to each other, and none provide confluence.
What traders know (and security should learn) is that the value isn’t in raw data — it’s in correlation.
It’s not just what’s happening… it’s what matters based on everything else happening too.
Until security platforms show risk in context, organizations will stay reactive and overwhelmed.
The Fix: A Control System Built for Decision-Making
Here’s what a Bloomberg-style security platform should offer:
- Unified visibility: Provide not just an asset inventory, but a live, interconnected model that shows relationships, risk, configuration posture and changes across the stack.
- Signal confluence: Combine alerts, posture checks, and business context into something that can be ranked, reasoned about, and acted on.
- Real-time response: Trigger policies or actions directly: isolate a workload, escalate a finding, adjust access, all within the same interface and/or workflow.
- Outcome tracking: Know what action was taken, why, and what happened next. Track posture like you’d track portfolio performance.
This isn’t theory — it’s where the best traders have been and the best platforms are headed. At imPAC, we’re building this with a federated, automation-first model. Signals come in, context is added, controls run, and results are tracked. Not in weeks. In minutes.
Security Needs to Get Off the Sidelines
The world doesn’t need more dashboards or alerts. It needs systems of decision and action.
Security is a business-critical domain. Teams shouldn’t be stuck interpreting alerts like reading tea leaves. They need clarity, control, and the confidence to act just like traders do, every second of every day.
So the question isn’t whether your security tools are “working.”
It’s whether they’re working like a high-stakes trading platform or an outdated fax machine.
Want to see what confluence, control, and real-time decision-making actually look like?


